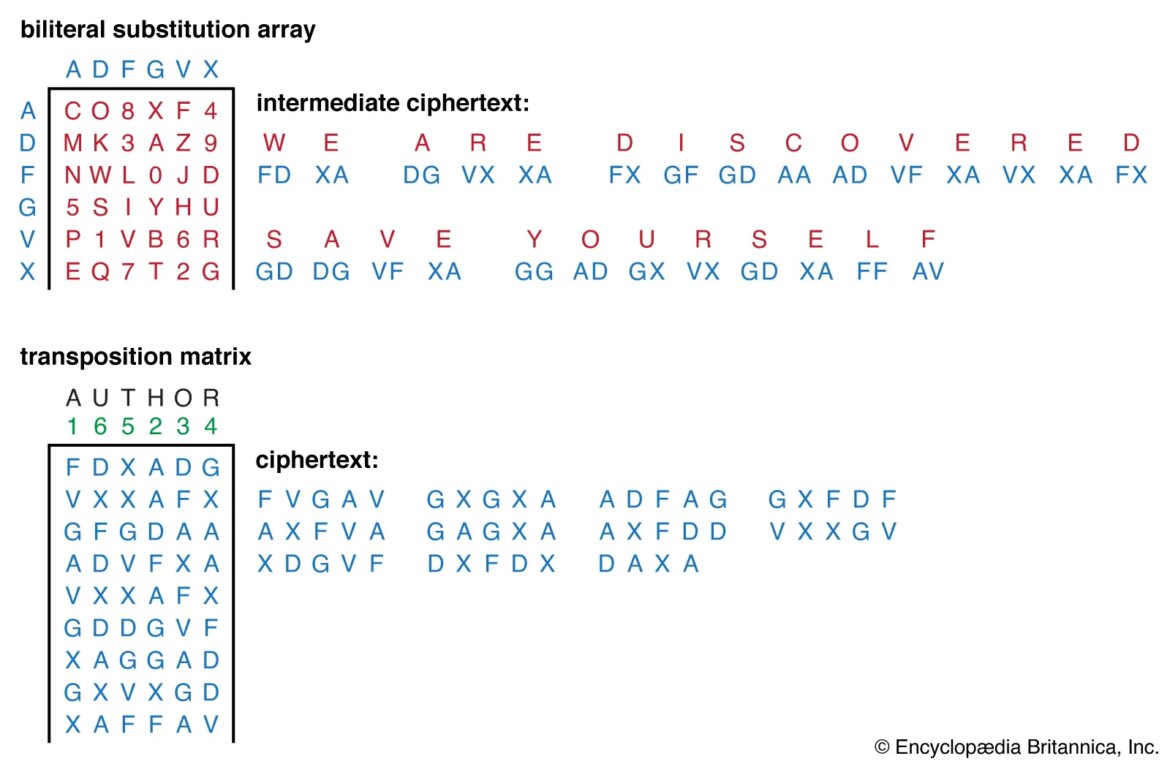
Cipher (also known as cypher) is an encryption technique used to secure data, typically for the purpose of protecting it from unauthorized access. Cipher is a type of cryptography, which is the practice and study of techniques used to protect information in transit or at rest. It involves transforming plain text into unintelligible ciphertext using a set of algorithms or transformations referred to as ciphers. Ciphers are primarily used by organizations such as banks and governments to prevent sensitive information from being accessed by outside parties.
Cipher can be divided into two primary categories: symmetric key cipher and asymmetric key cipher. Symmetric key ciphers use one single secret key that both sender and receiver must know in order to encrypt/decrypt messages while asymmetric key ciphers involve two separate keys, one public and one private, which are mathematically linked together but not necessarily known simultaneously by either party.
Symmetric-key ciphers have been around since ancient times when Julius Caesar famously employed a substitution cipher called the Caesar Cipher during his military campaigns in Gaul over 2000 years ago; however modern cryptographic systems make use of much more sophisticated algorithms than those employed during this period. Examples include Data Encryption Standard (DES), Advanced Encryption Standard (AES), Triple DES (3DES) and International Data Encryption Algorithm (IDEA).
Asymmetric-key ciphers were first proposed in 1976 with Diffie-Hellman Key Exchange and subsequently formalized with RSA algorithm developed by Rivest et al., which remains widely popular today due its relatively high security level when properly implemented despite its age compared other newer algorithms like Elliptic Curve Cryptography (ECC). Asymmetric-key ciphers employ mathematical functions based on prime factorization problems along with other advanced algorithmic techniques such as elliptic curve cryptography which provides higher levels of security against brute force attacks compared to symmetrical methods alone even though they tend require longer computation times due their complexity.